File screens have successfully stopped Locky.
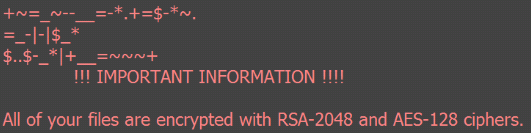
I ran a curious file today that gave me the picture above…but my file server is just fine.
For a test, I created multiple file shares.
One share did not have a screen enabled.
The other share had the screen configured as detailed in my previous two posts.
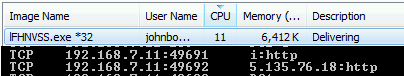
After running the email attachment, I observed this netstat and task information.
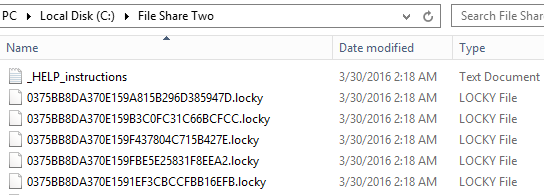
Here is what what is left of the share without the screen.
This is the share that had the screen enabled. I like this one better!
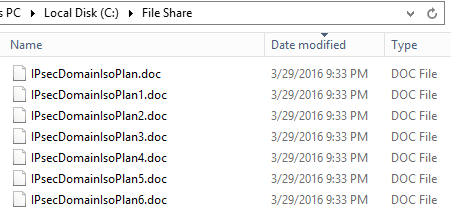
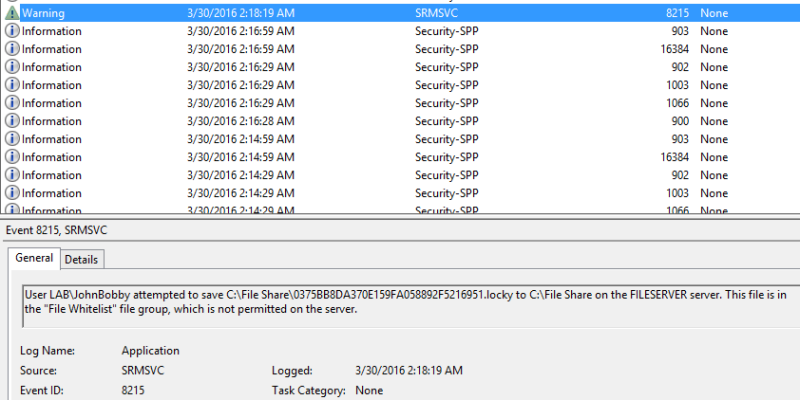
At 2:18, an event was logged in response to the .locky files. The path in this event is the path shown in the picture above. It is sorted by modified date to show that not even a single file was changed.
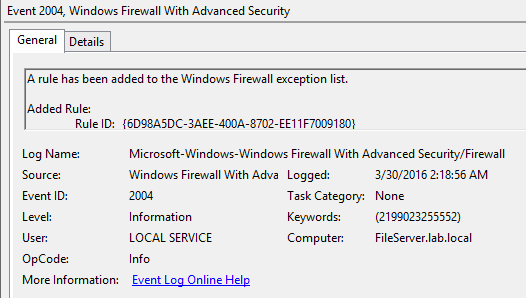
Here is the firewall creation event. This rule was created 37 seconds after the alert was triggered.
This may not work forever but it is proof enough for me to justify implementing in production. I hope this helps you too!
You could even take this another step further to protect PC data. If you configure your PCs with Desktop and Documents redirection on a screened share, even the PC data should be protected.
Time to revert my lab!
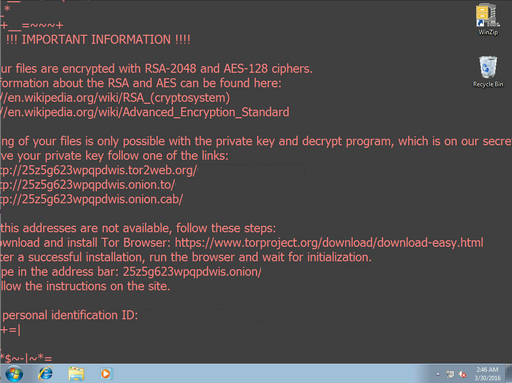

File screens work but this article over at Question Driven is very comprehensive. Check it out!
LikeLike
http://www.questiondriven.com/2016/03/07/how-to-prevent-ransomware-infections/
LikeLike